More a quick reference for me than anything else - these are the steps to enable https for iis on IaaS in Azure (well or anywhere for that matter) - this will use a 'proper' certificate from a certifying authority to stop all those warnings you get with self certified ones.
So here are the quick steps - in this case i have a server called testssl this is in an azure domain called mycompany.onmicrosoft.com however the certificate domain name i'm wanting to use is something different completely (but still a domain that we control) - i just wanted to show that there does not have to be a direct link between them - and it's a good job as microsoft own onmicrosoft.com so there is no way as an end customer to order certificates for this anyway.
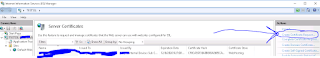
First up we go into IIS and vavigate to this screen and double click the server certificates option
Then we click create new request
Fill in a few details (note here I'm choosing this domain name that is not linked to the current server or the domain that that is in)
Choose some cipher properties
And choose a file to place the request in
This generates somethign like this which you'll likely be familiar with in some shape or form
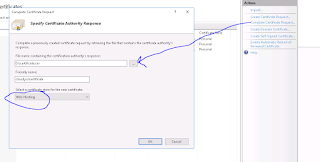
This then needs to be sent to some certifying authority who will then send you the matching certificate that pairs up to this original request. (we use quovadis but any vendor will do). Once you have this we need to import this new certificate (no cutting and pasting it has to be in a file) and select it is to be used for web hosting.
Then we can see that it loaded OK
Now we need to enable the https binding (shown in the pic below) along with setting the hostname we want to use (this is the one that is in the certificate and is nothing to do with the actual server hostname)
cloudyssl.something.something.com points at myactualhostname.mydomain.com
Once that is in place i can browse tp the default website on https port 443 and the site loads just fine and i get no certificate warnings - everything is happy - job done.








usefull article. Thanks for sharing.
ReplyDeleteThanks, great post.
ReplyDelete